Data Security in the Global Telecommunications Sector: A Deep Dive into the Latest Trends and Advancements
Related Article
- Cyber Insurance: The Price Tag Is Rising, But The Need Remains
- Don’t Let Travel Troubles Ruin Your Trip: A Guide To International Travel Insurance
- Decoding The Consumer Confidence Index: A Guide To Understanding The Economic Pulse
- The Road Ahead: Navigating Insurance Risks In The Age Of Self-Driving Cars
- The Elusive Shadow: Unpacking Economic Policy Uncertainty
Introduction
We warmly welcome you to explore Data Security in the Global Telecommunications Sector: A Deep Dive into the Latest Trends and Advancements with us.
Data Security in the Global Telecommunications Sector: A Deep Dive into the Latest Trends and Advancements
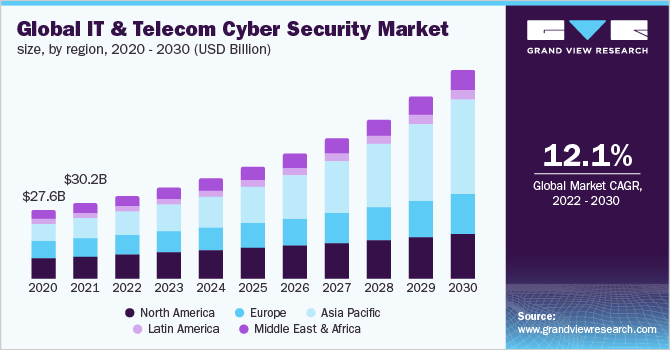
The global telecommunications sector is a complex and ever-evolving landscape, constantly pushing the boundaries of connectivity and innovation. But with this progress comes a critical challenge: safeguarding sensitive data. From customer information to network infrastructure, telecommunications companies are entrusted with vast amounts of data, making them prime targets for cyberattacks. This article delves into the crucial topic of data security in the global telecommunications sector, exploring the latest trends, advancements, and challenges faced by industry players.
The Ever-Growing Threat Landscape
The telecommunications sector faces a unique set of security challenges. With the rise of 5G and the Internet of Things (IoT), the attack surface is expanding rapidly. Hackers are increasingly targeting:
- Network Infrastructure: Compromising core network infrastructure can disrupt service, steal data, and even facilitate large-scale attacks.
- Customer Data: Personal information like names, addresses, and financial details are highly valuable to cybercriminals.
- Mobile Devices: Smartphones and other connected devices are vulnerable to malware and phishing attacks, potentially exposing user data.
- Cloud Services: Telecommunication companies are increasingly relying on cloud services, which introduces new security considerations.
Key Data Security Trends Shaping the Industry
The telecommunications sector is actively adapting to the evolving threat landscape with innovative solutions and strategies. Here are some key trends shaping the industry:
1. Zero Trust Security: This approach eliminates the concept of a trusted network perimeter and assumes that all users and devices are potentially untrusted. Zero Trust principles are implemented through granular access controls, multi-factor authentication, and continuous monitoring to minimize the impact of a potential breach.
2. Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are playing a crucial role in enhancing data security. They can be used for threat detection, anomaly detection, and automated incident response, enabling faster and more effective security operations.
3. Secure 5G Networks: As 5G networks roll out globally, ensuring their security is paramount. Security by design principles are being implemented, including encryption, authentication, and network slicing, to protect 5G infrastructure and data transmission.
4. Blockchain Technology: Blockchain offers a decentralized and tamper-proof ledger, making it ideal for secure data storage and management. It can be used for secure identity management, supply chain transparency, and preventing data manipulation.
5. Data Privacy Regulations: Global data privacy regulations like GDPR and CCPA are driving data security practices. Telecommunication companies are implementing data minimization, consent mechanisms, and robust data breach notification procedures to comply with these regulations.
Advancements in Data Security Technologies
Alongside these trends, the telecommunications industry is embracing advanced technologies to bolster data security:
1. Next-Generation Firewalls: Traditional firewalls are evolving to provide more sophisticated protection against advanced threats. Next-generation firewalls offer features like intrusion prevention, application control, and threat intelligence integration.
2. Endpoint Security Solutions: Securing endpoints like laptops, smartphones, and tablets is crucial. Endpoint security solutions offer real-time threat detection, malware prevention, and data loss prevention capabilities.
3. Security Information and Event Management (SIEM): SIEM solutions centralize security logs and events from various sources, enabling security teams to monitor, analyze, and respond to security incidents more effectively.
4. Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate repetitive security tasks, enabling faster incident response and reducing the burden on security teams.
5. Advanced Threat Intelligence: Leveraging threat intelligence feeds provides valuable insights into emerging threats and attack patterns, enabling proactive security measures.
Data Security in the U.S. Market: A Closer Look
The U.S. telecommunications market is a major player in the global landscape, facing similar security challenges and embracing similar trends. However, specific regulations and initiatives shape the U.S. data security landscape:
- The Cybersecurity and Infrastructure Security Agency (CISA): CISA plays a critical role in coordinating cybersecurity efforts across the U.S. government and private sector, providing guidance and resources to telecommunications companies.
- The Federal Communications Commission (FCC): The FCC regulates telecommunications services, including data security practices. It has established guidelines for protecting customer information and ensuring network security.
- The National Institute of Standards and Technology (NIST): NIST develops cybersecurity standards and frameworks, providing valuable guidance for telecommunications companies to implement effective data security practices.
- The California Consumer Privacy Act (CCPA): As a state-level regulation, the CCPA requires companies to provide consumers with transparency about their data collection and usage practices.
Expert Insights: Navigating the Data Security Landscape
"Data security is no longer a ‘nice-to-have’ but a fundamental requirement for success in the telecommunications industry," says Dr. Emily Carter, a leading cybersecurity expert. "Companies need to adopt a proactive and comprehensive approach to data security, incorporating cutting-edge technologies and robust security practices."
"The evolving threat landscape demands constant vigilance and adaptation," adds Mr. David Lee, CEO of a leading telecommunications security firm. "Investing in skilled security professionals, fostering a culture of security awareness, and collaborating with industry partners are crucial for building a resilient security posture."
FAQ: Addressing Common Questions
Q: What are the biggest challenges facing data security in the telecommunications sector?
A: The biggest challenges include the rapid growth of the attack surface, the sophistication of cyberattacks, the need for constant adaptation to new threats, and the shortage of skilled cybersecurity professionals.
Q: How can telecommunications companies improve their data security posture?
A: Companies can improve their security by implementing a comprehensive security strategy, embracing emerging technologies like AI and ML, fostering a strong security culture, and collaborating with industry partners.
Q: What role do data privacy regulations play in data security?
A: Data privacy regulations like GDPR and CCPA drive companies to adopt stricter data security practices, ensuring data is handled responsibly and securely.
Q: What are the key takeaways for telecommunication companies?
A: Data security is a continuous journey, not a destination. Telecommunication companies need to prioritize proactive security measures, invest in emerging technologies, and adapt to the ever-changing threat landscape.
Conclusion: Embracing a Secure Future
Data security is no longer a niche concern; it’s a core element of the telecommunications sector’s future. By embracing the latest trends, leveraging advanced technologies, and fostering a culture of security awareness, telecommunication companies can effectively protect their valuable data and maintain the trust of their customers.
Source URL: [Insert URL to relevant source material here]
Conclusion
We look forward to sharing more valuable knowledge in the future. Stay tuned for more exciting articles and updates!